Connect your Google Cloud Organization
Overview
To offer the full capabilities of the DoiT Platform, we request permissions to access the Google API and obtain information for monitoring or alerts, and help you act on recommendations if applicable.
Your DoiT account must have the Manage Settings permission.
Your Google Cloud account must have the Organization Role Administrator role to create and attach custom roles to service accounts under the organization.
Workload identity federation
Google Cloud supports using service accounts as identities for workloads. Starting June 2023, the preferred way to configure identities for DoiT Console workloads changes to workload identity federation. This method mitigates the security risks associated with service account keys.
To simplify the policy configuration and maintenance while offering an enhanced security posture, we leverage the service account impersonation feature, which involves two principals:
The privilege-bearing service account: Has the required permissions to access the target resource.
The caller: Needs to access the target resource but lacks the permissions.
Configure identities for DoiT workloads
When connecting DoiT Console to your organization, you need to perform the following tasks to configure the identities for DoiT workloads:
Create a service account with the permissions to access the relevant resources of your organization.
Grant the DoiT-owned service account
[email protected](the caller) permissions to impersonate the privilege-bearing service account.
Create a service account
To create a service account:
Log in to the DoiT Console, select the gear icon () from the top navigation bar, and then select Google Cloud.
Select Create a new service account.
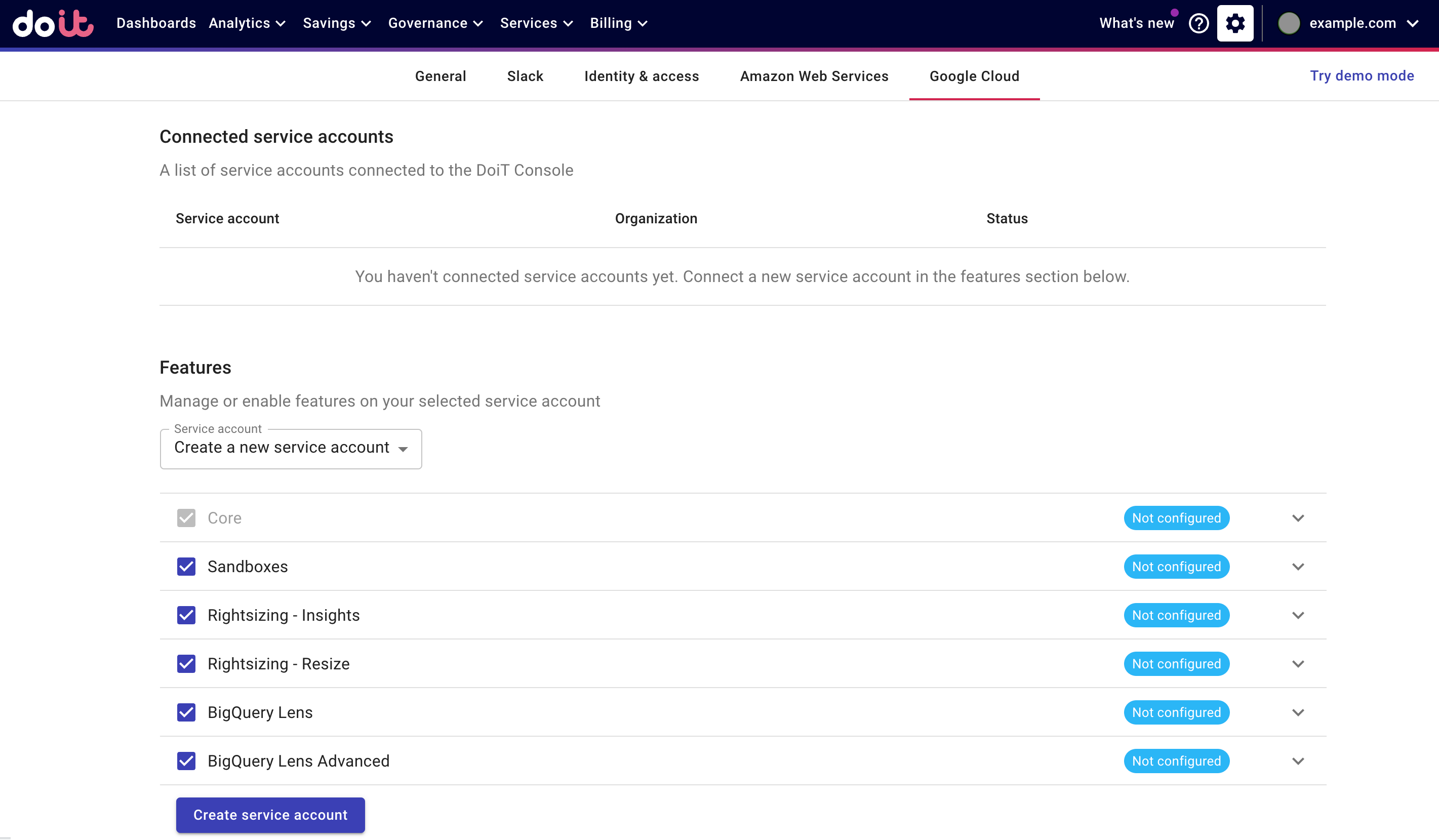
Select features to enable on your account. You can expand features to review the required permissions.
Select Create service account. You'll see the gcloud commands you need to run in the DoiT Console.
If you want to use a custom name for your service account, in the Create service account command, replace
doit-cmpby a custom name.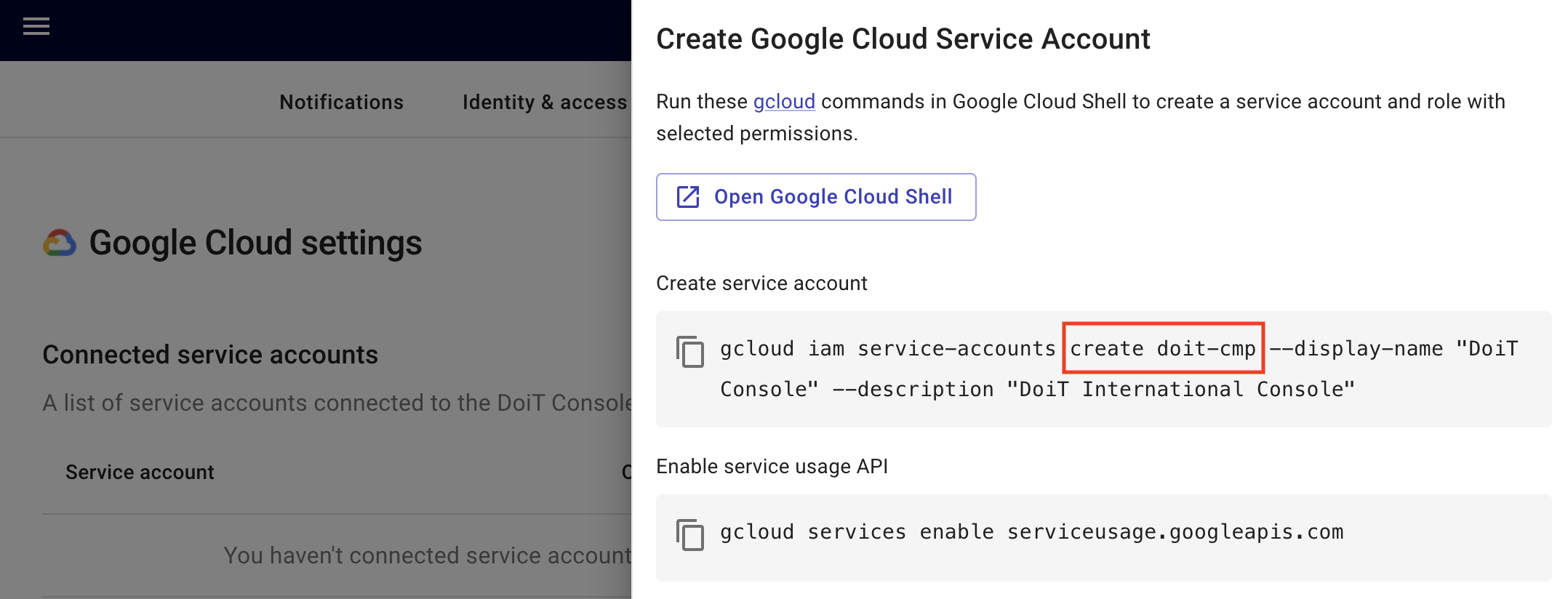 Edit a service account name
Edit a service account nameTo change the name of a service account after its creation, you need to remove the service account and create a new one with the updated name.
Start a Google Cloud Shell session (e.g., Launch the Cloud Shell Editor) and select a suitable Google Cloud project to create your service account.
Select a suitable Google Cloud projectThe project must belong to your organization.
The project must be connected to a Google Cloud Billing account (see Verify the billing status of your projects).
You intend to keep the project for the long term and make it accessible only to trusted people.
Run the commands sequentially to perform the following tasks:
Create a new service account in the current project.
Enable service usage API in the current project.
Create a custom role with the permissions required by your chosen features.
Add a policy binding with the custom role for the new service account.
NotePermissions are granted on the organization level. See Security and data access policy for more information.
Log in to the Google Cloud console, go to the Roles page and verify that you have created a
doit_cmp_rolelinked to the DoiT Service Account in your organization.
Allow service account impersonation
After creating the privilege-bearing service account of your organization, you need to grant the DoiT caller service account the Service Account Token Creator role roles/iam.serviceAccountTokenCreator to allow it to impersonate the former.
If you use GCP organization policy to restrict identities by domain, make sure to whitelist the DoiT caller service account [email protected] using its Organization Resource ID C03rw2ty2 before proceeding.
Run the following command:
gcloud iam service-accounts add-iam-policy-binding $YOUR_SA --member=serviceAccount:[email protected] --role=roles/iam.serviceAccountTokenCreator
Update role
To add or remove features on the service account:
Select the gear icon () from the top navigation bar, and then select Google Cloud.
Select your service account.
Modify the selection of features as needed.
Select Update role.
You'll be asked to run
gcloudcommands to update your service account's role.
For BigQuery Lens Advanced, you also need to enable Google Cloud Resource Manager API in the project where you create your service account.
Add multiple service accounts
If you have multiple Google Cloud organizations, you can create a service account for each organization to regulate which organization gets access to which features.
Remove service accounts
In case you need to remove a service account from the DoiT Console and then create a new one, be aware that:
Removing a service account from the DoiT Console also removes the related datasets and sinks created by BigQuery Lens.
Once the BigQuery Lens permissions are granted to the new service account, we'll re-create the sink and trigger historical jobs backfill, which may lead to increased costs during your service account setup.
Service accounts with account keys
If you have service accounts with account keys, to avoid potential connection issues, we strongly recommend keeping the account keys and also allowing service account impersonation.
Rotate service account keys
If you cannot fully migrate to workload identity federation yet and want to rotate the service account key, you need to remove the service account from the DoiT Console, create a new one, and then upload the new key JSON file.
Make sure you understand the consequences of removing service accounts from the DoiT Console before proceeding.