Link your AWS account
Link your AWS account to the DoiT Platform to unlock advanced functionalities such as proactive resource quota monitoring and Spot Scaling.
Required Permission: Manage Settings
Link an account
To link an account:
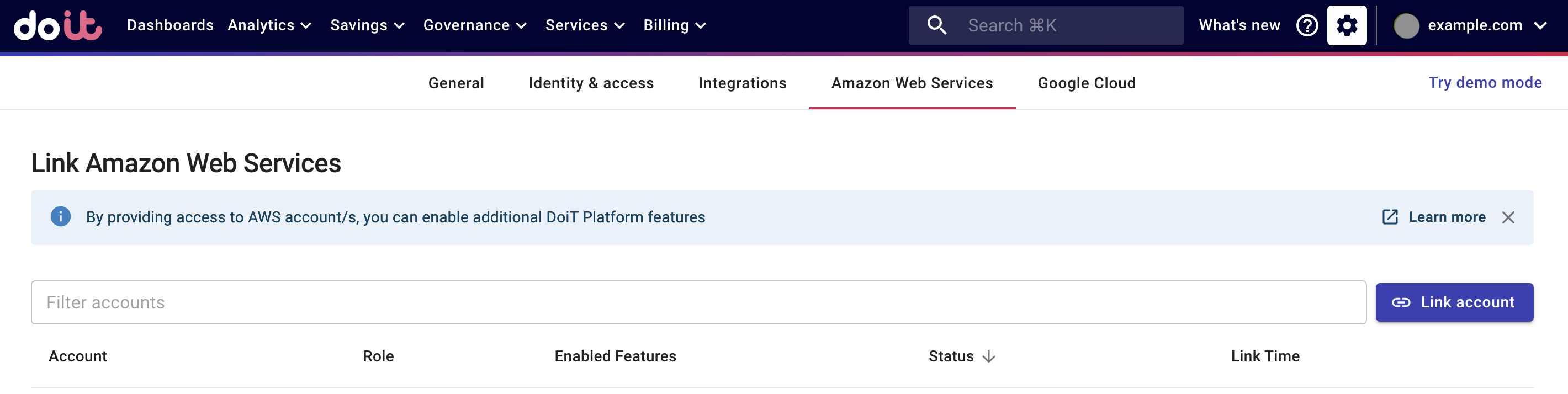
Log in to the DoiT Console, select the gear icon () from the top navigation bar, and then select Amazon Web Services.
On the Link Amazon Web Services page, select Link account.
Proceed to create an AWS IAM Role with the required policies.
Create a role automatically
Select Create a role automatically.
Select features to enable on the your AWS account. You can select the expand button to the left of the feature name to review the required AWS policies.
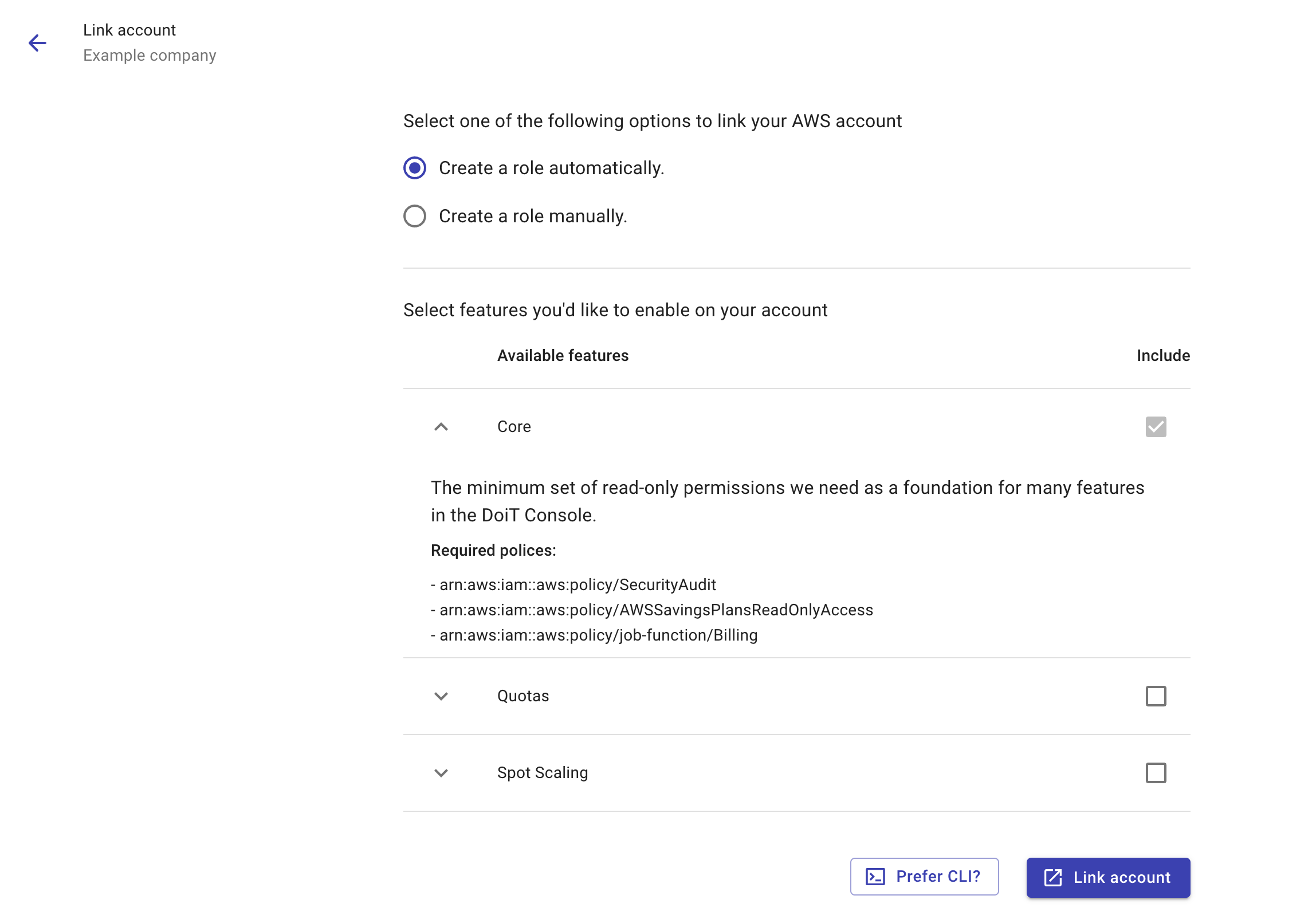
Create a CloudFormation stack for the IAM role by using one of the following options.
Using AWS CloudFormation console:
Select Link account to launch the DoiT stack template in the AWS CloudFormation console.
Make sure that you are in the
US East (N. Virginia) us-east-1region.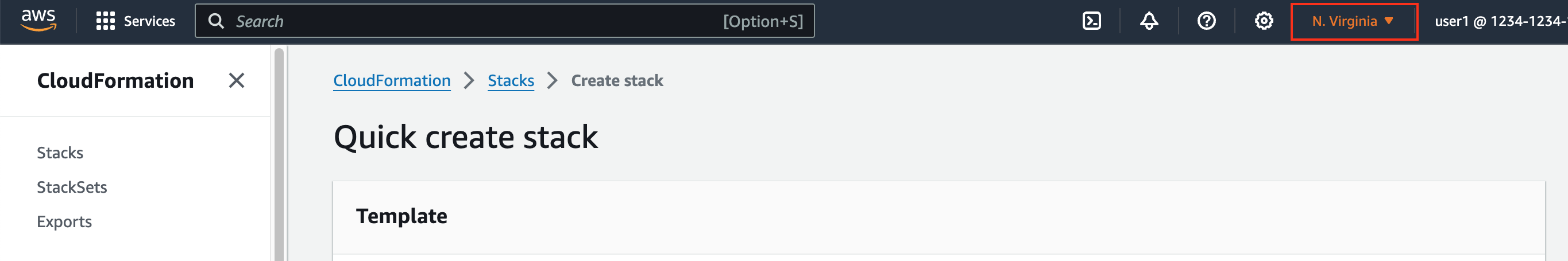
Select the checkbox at the bottom of the page to acknowledge that AWS CloudFormation might create IAM resources with custom names.
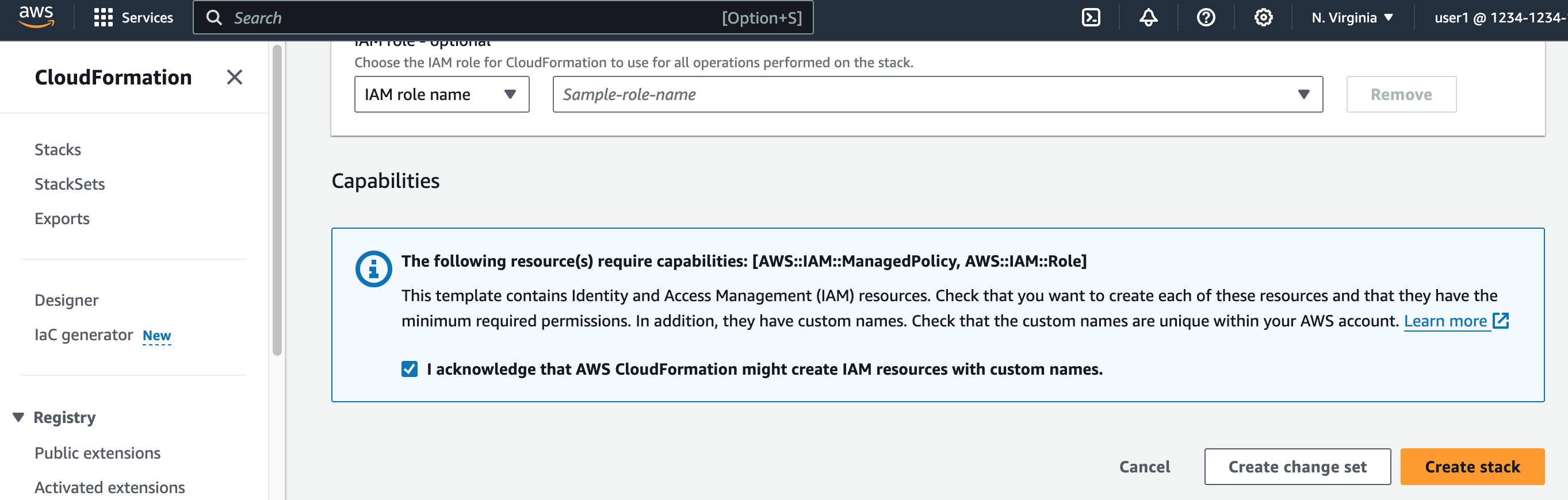
Create the stack.
Using AWS CloudShell:
Select Prefer CLI.
Copy the command from the pop-up window.
CautionIf you edit the CLI command before execution, you must keep the region to
us-east-1.Run the command in AWS CloudShell to create the specified CloudFormation stack.
After creating the stack, it may take up to 30 seconds for the account to link to the DoiT Platform. If the link attempt was successful, your linked AWS account will show a Healthy status.
Create a role manually
Select Create a role manually. Note down the listed
Our AWS AccountandYour External ID.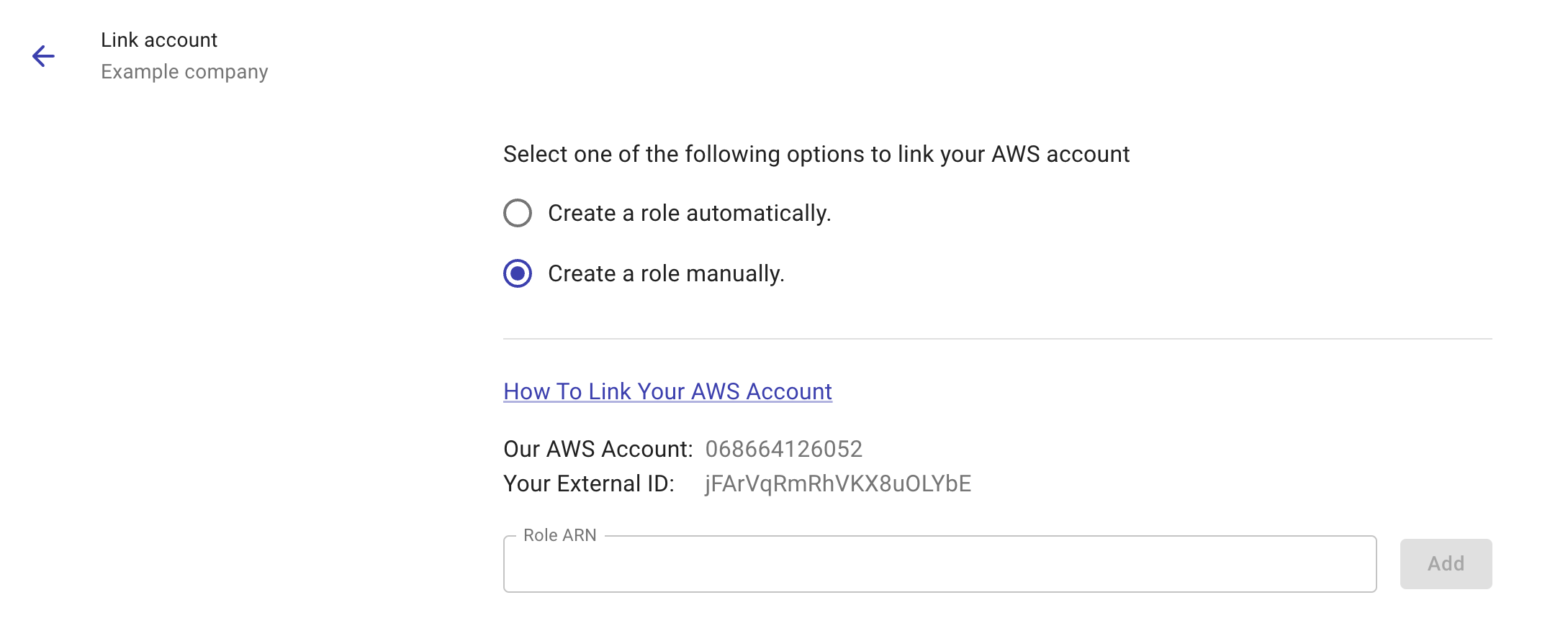
Create an AWS IAM Role.
Log in to the AWS Management Console, go to the IAM console, and select Roles in the left-hand side navigation pane.
See alsoAWS Documentation: Creating an IAM role (console)
Select Create role.
Select AWS account as the trusted entity.
Select Another AWS account and enter the DoiT AWS account ID (the
Our AWS Accountin the previous step).Select the checkbox
Require external IDand enter your external ID.Select Next to add permissions.
Choose policies in accordance with the features to enable:
For Core, add specific AWS managed policies to your role.
For Quotas and Spot Scaling, create custom policies by selecting Create policy, switching to the JSON tab, and then pasting the Quota monitoring permissions or the Spot Scaling permissions as the JSON policy document.
See alsoAWS Documentation: Creating IAM policies (console)
Once the policies are created, go back to your original tab. You may need to refresh to see the new policies in the search list.
Select all the new policies for the features you want to enable in addition to the three built-in policies required for Core features.
Select Next, give the Role an identifiable name , review the selected policies, and then select Create role.
After creating the role, select the role name to open its summary page, copy the value of the role's ARN, and paste the Role ARN to the DoiT Console.
Select Add to link your AWS account.
If successfully, the status of your AWS account will show as Healthy in the DoiT Console.
Feature permissions
Below are the required permissions for the features you can enable for a linked account.
Core
Core permissions are a minimum set of read-only permissions for many DoiT Platform features. It consists of the following AWS managed policies:
| AWS managed policy | Description |
|---|---|
SecurityAudit | Grants access to read security configuration metadata. |
AWSSavingsPlansReadOnlyAccess | Provides read-only access to Savings Plans service. |
Billing | Grants permissions for billing and cost management. |
Spot Scaling
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"ec2:Describe*",
"ec2:CreateLaunchTemplate",
"ec2:CreateLaunchTemplateVersion",
"ec2:ModifyLaunchTemplate",
"ec2:RunInstances",
"ec2:TerminateInstances",
"ec2:CreateTags",
"ec2:DeleteTags",
"ec2:CreateLaunchTemplateVersion",
"ec2:CancelSpotInstanceRequests",
"autoscaling:CreateOrUpdateTags",
"autoscaling:UpdateAutoScalingGroup",
"autoscaling:Describe*",
"autoscaling:AttachInstances",
"autoscaling:BatchDeleteScheduledAction",
"autoscaling:BatchPutScheduledUpdateGroupAction",
"cloudformation:ListStacks",
"cloudformation:Describe*",
"iam:PassRole",
"events:PutRule",
"events:PutTargets",
"events:PutEvents"
],
"Resource": "*",
"Effect": "Allow"
}
]
}
Quota Monitoring
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"support:DescribeTrustedAdvisorCheckSummaries",
"support:DescribeTrustedAdvisorCheckRefreshStatuses",
"support:DescribeTrustedAdvisorChecks",
"support:DescribeSeverityLevels",
"support:RefreshTrustedAdvisorCheck",
"support:DescribeSupportLevel",
"support:DescribeCommunications",
"support:DescribeServices",
"support:DescribeIssueTypes",
"support:DescribeTrustedAdvisorCheckResult",
"trustedadvisor:DescribeNotificationPreferences",
"trustedadvisor:DescribeCheckRefreshStatuses",
"trustedadvisor:DescribeCheckItems",
"trustedadvisor:DescribeAccount",
"trustedadvisor:DescribeAccountAccess",
"trustedadvisor:DescribeChecks",
"trustedadvisor:DescribeCheckSummaries"
],
"Resource": "*"
}
]
}
Edit linked accounts
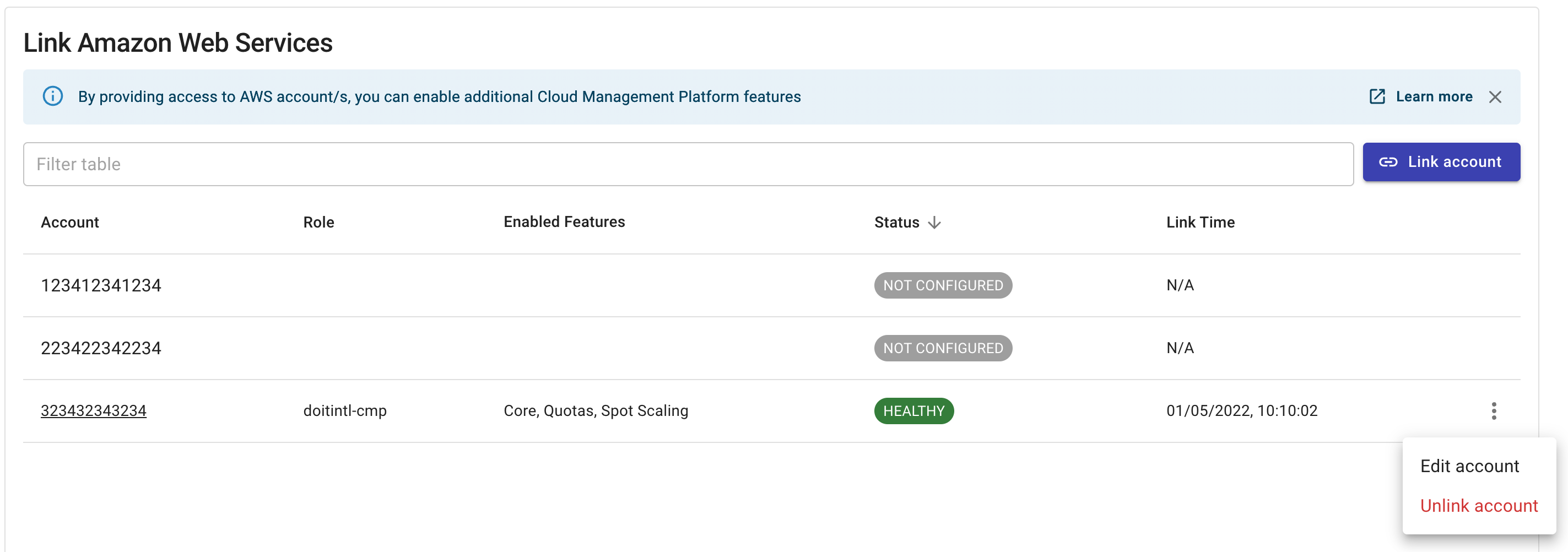
Unlink an account
To unlink an account:
Navigate to the Link Amazon Web Services page.
Locate the account of interest.
Select the three dots menu (⋮) at the rightmost end of the account entry.
Select Unlink account.
Modify feature access
Add a feature
To add a new feature, you need to update the IAM role of the linked account with additional permissions:
Select the three dots menu (⋮) at the rightmost end of the account entry.
Select Edit account.
Select the checkbox of the new feature.
Update the IAM role with the new permissions by using one of the following options.
Select Update account to create a CloudFormation stack in the AWS console.
Select Prefer CLI to get the command to create the CloudFormation stack via AWS CloudShell.
See Create a role automatically for more information.
Remove a feature
To remove a feature:
Go to the IAM page in the AWS console.
Detach the policies associated with the feature in the linked account's role.